Jan 30, 2019 A model validation toggle feature was added to the tool's Options menu. Several links in the threat properties were updated. Minor UX changes were made to the tool's home screen. The Threat Modeling Tool now inherits the TLS settings of the host operating system and is supported in environments that require TLS 1.2 or later. Microsoft Threat Modeling Tool. Microsoft Threat Modeling Tool is one of the oldest and most tested threat modeling tools in the market. It is an open-source tool that follows the spoofing, tampering, repudiation, information disclosure, denial of service, and elevation of privilege (STRIDE) methodology. A model validation toggle feature was added to the tool's Options menu. Several links in the threat properties were updated. Minor UX changes were made to the tool's home screen. The Threat Modeling Tool now inherits the TLS settings of the host operating system and is supported in environments that require TLS 1.2 or later. The Microsoft Threat Modeling Tool Importer Extension library adds a button in the Import ribbon: Import Document in the MS TMT section. The Import ribbon. If you click this button, you will be offered the opportunity to select the Threat Model (.TM7) or template (.TB7) to be imported. After a fast processing, you should see a Threat Modeling. Microsoft Threat Modeling Tool The Microsoft Threat Modeling Tool makes threat modeling easier for all developers through a standard notation for visualizing system components, data flows, and security boundaries. It also helps threat modelers identify classes of threats they should consider based on the structure of their software design.
- Microsoft Threat Modeling Tool 2014
- Microsoft Threat Modeling Tool 2016
- Microsoft Threat Modeling Tool Aws
- Microsoft Threat Modeling Tool Uses Threat Classification Scheme

The Threat Modeling Tool is a core element of the Microsoft Security Development Lifecycle (SDL). It allows software architects to identify and mitigate potential security issues early, when they are relatively easy and cost-effective to resolve. As a result, it greatly reduces the total cost of development. Also, we designed the tool with non-security experts in mind, making threat modeling easier for all developers by providing clear guidance on creating and analyzing threat models.
The tool enables anyone to:
Microsoft Threat Modeling Tool 2014
- Communicate about the security design of their systems
- Analyze those designs for potential security issues using a proven methodology
- Suggest and manage mitigations for security issues
Here are some tooling capabilities and innovations, just to name a few:
- Automation: Guidance and feedback in drawing a model
- STRIDE per Element: Guided analysis of threats and mitigations
- Reporting: Security activities and testing in the verification phase
- Unique Methodology: Enables users to better visualize and understand threats
- Designed for Developers and Centered on Software: many approaches are centered on assets or attackers. We are centered on software. We build on activities that all software developers and architects are familiar with -- such as drawing pictures for their software architecture
- Focused on Design Analysis: The term 'threat modeling' can refer to either a requirements or a design analysis technique. Sometimes, it refers to a complex blend of the two. The Microsoft SDL approach to threat modeling is a focused design analysis technique
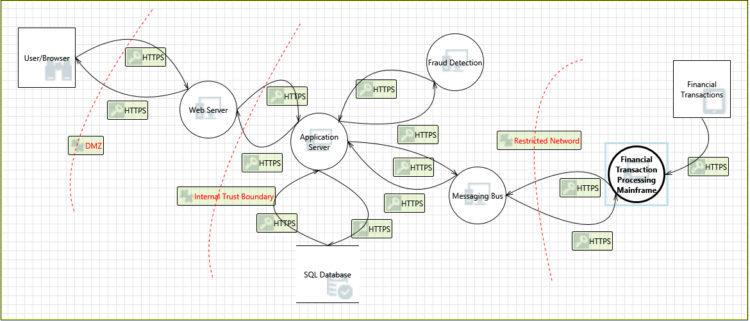
Next steps
The table below contains important links to get you started with the Threat Modeling Tool:See also: System requirements
| Step | Description |
|---|---|
| 1 | Download the Threat Modeling Tool |
| 2 | Read Our getting started guide |
| 3 | Get familiar with the features |
| 4 | Learn about generated threat categories |
| 5 | Find mitigations to generated threats |
Microsoft Threat Modeling Tool 2016

Microsoft Threat Modeling Tool Aws
Resources
Here are a few older articles still relevant to threat modeling today:
Microsoft Threat Modeling Tool Uses Threat Classification Scheme
Check out what a few Threat Modeling Tool experts have done: