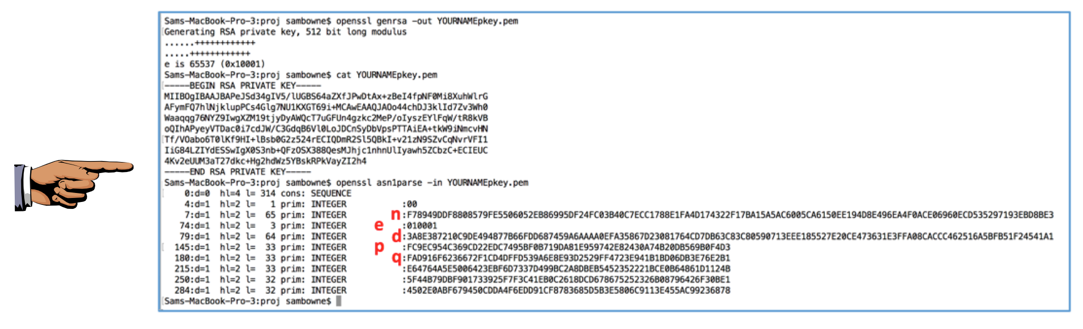
RSA Encryptor/Decryptor/Key Generator/Cracker. To generate a key pair, just click the Generate button. How to Generate a SSH Key Pair. When generating SSH keys under Linux, you can use the ssh-keygen command. It is a tool for creating new authentication key pairs for SSH. To generate a SSH key pair open up the terminal and type in the following command: ssh-keygen -t rsa Generating public/private rsa key pair. Enter file in which to save the key.
- The only required parameter to generate an RSA key pair is the key length, which should be at least 2048 bits.
- It generates a pair of keys in /.ssh directory by default. You now have two files: idrsa (the private key). The private key is stored on your local computer and should be kept secure, with permissions set so that no other users on your computer can read the file. Idrsa.pub (the public key). The public key is placed on the server you intend to log in to.
If you plan to push/pull using SSH, you need to set up SSH keys. You want to do this (or cache your username and password, chapter 10), so you don’t have to authenticate yourself interactively with GitHub over and over again. I suggest you set up one of these methods of authentication on each computer you want to connect to GitHub from.
11.1 SSH keys
SSH keys provide a more secure way of logging into a server than using a password alone. While a password can eventually be cracked with a brute force attack, SSH keys are nearly impossible to decipher by brute force alone. Generating a key pair provides you with two long strings of characters: a public and a private key. You can place the public key on any server (like GitHub!), and then unlock it by connecting to it with a client that already has the private key (your computer!). When the two match up, the system unlocks without the need for a password. You can increase security even more by protecting the private key with a passphrase.
Adapted from instructions provided by GitHub and Digital Ocean.
11.2 SSH outline and advice
High level overview of what must happen:
- Create a public-private SSH key pair. Literally, 2 special files, in a special place. Optionally, encrypt the private key with a passphrase (best practice).
- Add the private key to your ssh-agent. If you protected it with a passphrase, you may have additional configuration.
- Add your public key to your GitHub profile.
Riello dld 800 manual. Advice:
- If you are new to programming and the shell, you’ll probably find HTTPS easier at first (chapter 10). You can always switch to SSH later. You can use one method from computer A and the other from computer B.
- You should swap out your SSH keys periodically. Something like once a year.
- It’s best practice to protect your private key with a passphrase. This can make setup and usage harder, so if you’re not up for that (yet), either don’t use a passphrase or seriously consider using HTTPS instead.
- Don’t do weird gymnastics in order to have only one key pair, re-used over multiple computers. You should probably have one key per computer (I do this). Some people even have one key per computer, per service (I do not do this).
- It is normal to associate multiple public keys with your GitHub account. For example, one public key for each computer you connect with.
11.3 Do you already have keys?
You can check this from RStudio or from the shell.
Global advice: if you do have existing keys, but have no clue where they came from or why you created them, you should seriously consider creating a new SSH key pair. It’s up to you to figure out whether/how to delete the old ones. But don’t let that keep you from creating new keys and moving forward.
11.3.1 From RStudio
Go to Tools > Global Options…> Git/SVN. If you see something like ~/.ssh/id_rsa in the SSH RSA Key box, you definitely have existing keys. Caveat: RStudio only looks for a key pair named id_rsa and id_rsa.pub. This makes sense, because it’s the default and very common. But SSH keys can have other names. If you want to be completely certain, you should also check in the shell.
11.3.2 From the shell
Go to the shell (appendix A).
List existing keys:
If you are told ~/.ssh/ doesn’t exist, you don’t have SSH keys!
If you see a pair of files like id_rsa.pub and id_rsa, you have a key pair already. The typical pattern is id_FOO.pub (the public key) and id_FOO (the private key). If you’re happy to stick with your existing keys, skip to the sections about adding a key to the ssh-agent and GitHub.
11.4 Create an SSH key pair
11.4.1 Option 1: Set up from RStudio
Go to Tools > Global Options…> Git/SVN > Create RSA Key….
RStudio prompts you for a passphrase. It is optional, but also a best practice. Configuring your system for smooth operation with a passphrase-protected key introduces more moving parts. If you’re completely new at all this, skip the passphrase (or use HTTPS!) and implement it next time, when you are more comfortable with system configuration. I did not use a passphrase at first, but I do now, and record it in a password manager.
Click “Create” and RStudio will generate an SSH key pair, stored in the files ~/.ssh/id_rsa and ~/.ssh/id_rsa.pub.
11.4.2 Option 2: Set up from the shell
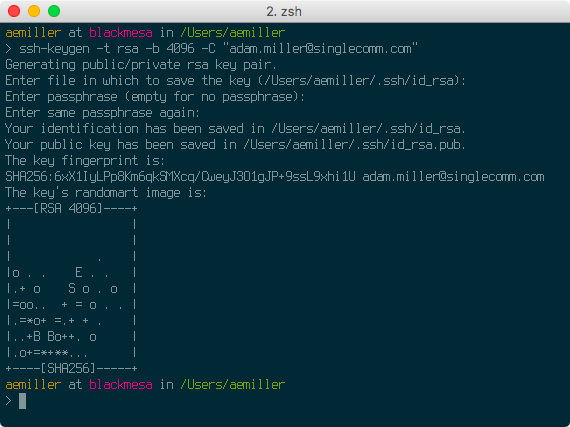
Create the key pair like so, but substitute a comment that means something to you, especially if you’ll have multiple SSH keys in your life. Consider the email associated with your GitHub account or the name of your computer, e.g. you@example.com or 2018-mbp.
Accept the proposal to save the key in the default location. Just press Enter here:
You have the option to protect the key with a passphrase. It is optional, but also a best practice. Configuring your system for smooth operation with a passphrase-protected key introduces more moving parts. If you’re completely new at all this, skip the passphrase and implement it next time, when you are more comfortable with system configuration. I did not use a passphrase at first, but I do now, and record it in a password manager.
The process should complete now and should have looked like this:
11.4.3 Add key to ssh-agent
Tell your ssh-agent about the key and, especially, set it up to manage the passphrase, if you chose to set one.
Things get a little OS-specific around here. When in doubt, consult GitHub’s instructions for SSH, which is kept current for Mac, Windows, and Linux.
11.4.3.1 Mac OS
Make sure ssh-agent is enabled. Here’s what success look like:
Processmaker cracked. Sometimes this fails like so:
A similar failure might be reported as “Permission denied”. You should try again, but as the superuser. Don’t forget to use exit to go back to your normal user account, when you are done!
Add your key to the ssh agent. If you set a passphrase, you’ll be challenged for it here. Give it. The -K option stores your passphrase in the keychain.
If you’re using a passphrase AND on macOS Sierra 10.12.2 and higher, you need to do one more thing. Create a file ~/.ssh/config with these contents:
This should store your passphrase persistently in the keychain. Otherwise, you will have to enter it every time you log in. Useful StackOverflow thread: How can I permanently add my SSH private key to Keychain so it is automatically available to ssh?.
11.4.3.2 Windows
In a Git Bash shell, make sure ssh-agent is running:
Add your key.
11.4.3.3 Linux
Detailed Steps To Create An SSH Key Pair - Azure Virtual ..
In a shell, make sure ssh-agent is running:
Add your key.
11.5 Provide public key to GitHub
Now we store a copy of your public key on GitHub.
11.5.1 RStudio to clipboard
Go to Tools > Global Options…> Git/SVN. If your key pair has the usual name, id_rsa.pub and id_rsa, RStudio will see it and offer to “View public key”. Do that and accept the offer to copy to your clipboard. If your key pair is named differently, use another method.
11.5.2 Shell to clipboard
Copy the public key onto your clipboard. For example, open ~/.ssh/id_rsa.pub in an editor and copy the contents to your clipboard. Or do one of the following at the command line:
- Mac OS:
pbcopy < ~/.ssh/id_rsa.pub - Windows:
clip < ~/.ssh/id_rsa.pub - Linux:
xclip -sel clip < ~/.ssh/id_rsa.pub
Linux: if needed, install via apt-get or yum. For example, sudo apt-get install xclip.
11.5.3 On GitHub
Make sure you’re signed into GitHub. Click on your profile pic in upper right corner and go Settings, then SSH and GPG keys. Click “New SSH key”. Paste your public key in the “Key” box. Give it an informative title, presumably related to the comment you used above, during key creation. For example, you might use 2018-mbp to record the year and computer. Click “Add SSH key”.
In theory, we’re done! You can use ssh -T git@github.com to test your connection to GitHub. If you’re not sure what to make of the output, see the link for details. Of course, the best test is to work through the realistic usage examples elsewhere in this guide.
11.6 Troubleshooting
11.6.1 HTTPS vs SSH
If you think you have SSH set up correctly and yet you are still challenged for credentials, consider this: for the repo in question, have you possibly set up GitHub, probably called origin, as an HTTPS remote, instead of SSH?
How to see the remote URL(s) associated with the current repo in the shell:
An SSH remote will look like this:
whereas an HTTPS remote will look like this:
You can toggle between these with git remote set-url:
11.6.2 git2r – or some other tool – can’t find SSH keys on Windows
Have you seen this error message?
We’ve seen it when working with Git/GitHub from R via the git2r package, which is used under the hood by many R packages, such as devtools, ghit, and usethis.
git2r uses the libgit2 library, not the Git you installed. This means you can have SSH keys configured properly for Git work in a Git Bash shell and from RStudio and still have problems with git2r! Ugh.
The root cause is confusion about the location of .ssh/ on Windows. R’s idea of your home directory on Windows often differs from the default location of config files for Git and ssh, such as .ssh/. On *nix systems, these generally coincide and there’s no problem.
Two important directories on Windows are the user’s HOME and USERPROFILE. R usually associates ~ with HOME, but Git and ssh often consult USERPROFILE for their config files. On my Windows 10 VM, I see:
Two workarounds:
Tell git2r explicitly where to find your public and private key. Example using
usethis::use_github():Create a symbolic link so that
.ssh/in R’s home directory points to your actual.ssh/directory. Example contributed by Ian Lyttle on Windows 7 using Command Prompt:
Finally, if git2r seems unable to get your SSH passphrase from ssh-agent, install the getPass package:
and git2r should launch a popup where you can enter your passphrase. Thanks to Ian Lyttle for this tip.
This link provides a great explanation of the uncertainty about where .ssh/ and user’s .gitconfig are located on Windows: git on Windows - location of configuration files. Bottom line: locate where your main tool expects and create symbolic links to help other tools find this stuff.
11.6.3 Other
Other things to double-check:
- Did you add the SSH to your ssh-agent?
- Did you configure Mac OS Sierra or High Sierra to persistently store your passphrase in the keychain?
- Did you add the public key to GitHub?
This tutorial series will teach you how to use GPG in Linux terminal. I will not tell you a bunch of theory to overwhelm you. Instead, I show you quick and dirty examples to get you started, and explain the basic theory along the way.
The tutorial series is divided into 4 parts:
- Part 1: Generate Your Keypair
This is part 1 of this series. At the end of this post, you should be able to generate your own public/private keypair and a revocation certificate. This certificate is used to revoke your public/private keypair when your private key is compromised or you forget the passphrase for your private key.
GPG can be used for encryption and for signing. This software is pre-installed on most Linux distributions. Currently the stable version is GPG 2.0. I’m using the modern version GPG 2.2 on Arch Linux.
Check Your GPG Version
First Let’s check out the version of GPG on your system and some interesting tidbits. Run the following command.
As you can see, I’m using GPG 2.2.8, which is the latest version. We also know that the configuration directory is ~/.gnupg, which will hold our public/private key files. The default option file is ~/.gnupg/gpg.conf and ~/.gnupg/dirmngr.conf. It also tells us what algorithms are supported.
If you look closely, you can see that the insecure hash algorithm SHA1 is still supported in version 2.2.8 SHA1 is obsolete and you don’t want to use it to generate signature.
Create Your Public/Private Key Pair and Revocation Certificate
Use gpg --full-gen-key command to generate your key pair.
It asks you what kind of key you want. Notice there’re four options. Sibelius 8 free mac. The default is to create a RSA public/private key pair and also a RSA signing key. Let’s hit Enter to select the default.
Next it asks you the key length. The default is 2048 bits long. 1024 RSA key is obsolete. The longer 4096 RSA key will not provide more security than 2048 RSA key. So hit Enter to select the default.
After that it asks you how long the key should be valid, 2 years is fine. You can always update the expiration time later on.
Now it asks you if it’s correct. Notice that the default is No. So press y then Enter to confirm it’s correct.
And now we need to provide some user identification information for the key. This is important because this information will be included in our key. It’s one way of indicating who is owner of this key. The email address is a unique identifier for a person. You can leave Comment blank.
Select Okay.
Now it asks you to enter a passphrase to protect your private key. Enter a good and long passphrase and remember it. Because if you forget this passphrase, you won’t be able to unlock you private key.
Once you enter and confirm your passphrase. GPG will generate your keys.
It will take a while for GPG to generate your keys. So you can now do other stuff.
It took about 4 minutes on my system to generate my key pair.
This first line tells us that GPG created a unique identifier for public key. This unique identifier is in hex format. When someone wants to download you public key, they can refer to you public key via your email address or this hex value.
The third line tells us that GPG created a revocation certificate and its directory.Your should never share you private key with anyone.If you private key is compromised, you can use revocateion certificate to revoke your key. That means you tell the rest of the world that the old public key shall not be used any more.I suggest that you open this revocation certificate with your text editor to see what’s inside there.
Let’s look at the last three lines. They tell us the public key is 2048 bits using RSA algorithm. The public key ID 4F0BDACC matchs the last 8 bits of key fingerprint. The key fingerprint is a hash of your public key.
It also lists our user ID information: your name and your email address. And it also indicates the subkey which is 2048 bits using RSA algorithm and the unique identifier of the subkey.
Now you can find that there are two files created under ~/.gnupg/private-keys-v1.d/ directory. These two files are binary files with .key extension.
Export Your Public Key
Others need your public key to send encrypted message to you and only your private key can decrypt it. Use the following command to export your public key. --armor option means that the output is ASCII armored. The default is to create the binary OpenPGP format. user-id is your email address.
The exported public key is written to pubkey.asc file.
Export Your Private Key
Issue the following command to export your private key.
The exported key is written to privkey.asc file.
Generating Public/Private Keys In C# And .NET
Protect Your Private Key and Revocation Certificate
Your private key should be kept in a safe place, like an encrypted flash drive. Treat it like your house key. Only you can have it and don’t lose it. And you must remember your passphrase, otherwise you can’t unlock your private key.
You should also protect your revocation certificate. If others have your revocation certificate, they can immediately revoke your public/private keypair and generate a fake public/priavte keypair.
Generate Rsa Key Pair Cisco
In part 2 we will look at how to encrypt message with your public key and how to decrypt it with your private key. Take care!